
 OPIX Systems, LLC
Master Systems Integrators
OPIX Systems, LLC
Master Systems Integrators
Building Management Simplified

About Us
Our Mission
OPIX stands for Open & Proprietary Information Exchange. Our mission is to simplify building management systems. We seek to empower our customers with intuitive and easy to learn tools.
Read More
About US
Company Profile
OPIX Systems was founded in 2017 by Managing Partners Jim Leaper and Charlie Garcia, following Josh Bedenbaugh in 2021. Since that time OPIX has grown at an exceptional rate.
Read More
Automation
Systems Integration
Integrate any system into a simple, easy to monitor and schedule dashboard. If you can dream it, we can find a way to integrate it into your building automation system.
Integration
Lighting Services
Design & Upgrades
OPIX has the technical and aesthetic training to help you implement a lighting solution that creates the best environment for your facilities needs while also saving energy.
Intelligent Lighting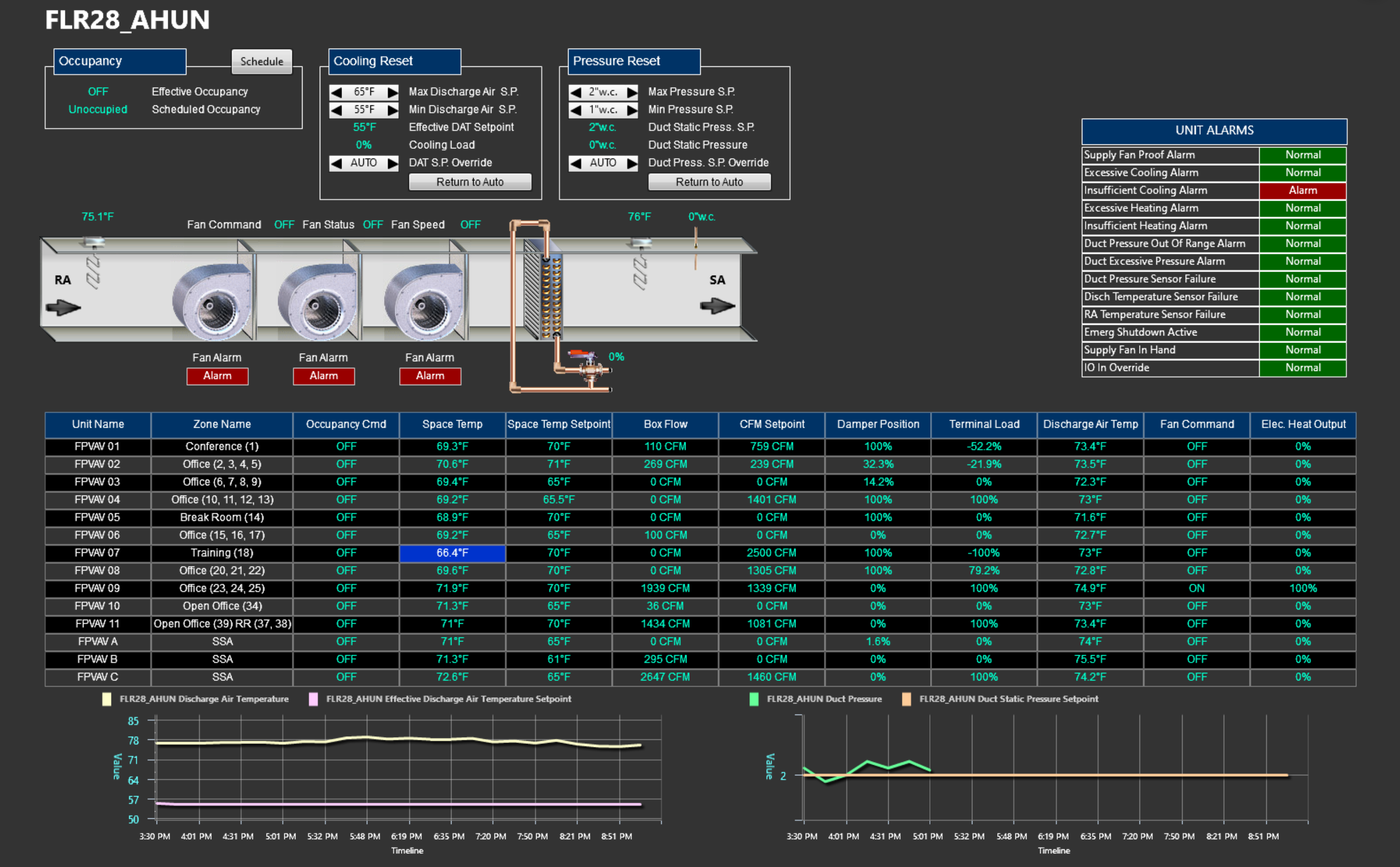
Graphics









